Prepared by:
HALBORN
Last Updated 04/01/2025
Date of Engagement: March 26th, 2025 - April 1st, 2025
Summary
100% of all REPORTED Findings have been addressed
All findings
27
Critical
0
High
1
Medium
3
Low
7
Informational
16
Table of Contents
- 1. Introduction
- 2. Assessment summary
- 3. Test approach and methodology
- 4. Static analysis report
- 5. Risk methodology
- 6. Scope
- 7. Assessment summary & findings overview
- 8. Findings & Tech Details
- 8.1 Impossibility to withdraw assets across protocols
- 8.2 Missing tvl limit check in default protocol deposits
- 8.3 Tvl limit bypass on first deposit
- 8.4 Revenue loss due to missing fee processing in withdrawfees()
- 8.5 Unallocated funds without notification when protocols reach tvl limits
- 8.6 Tvl limit bypass after complete withdrawal
- 8.7 Single step ownership transfer process
- 8.8 Use of non-compliant tokens may break contract functionality
- 8.9 Default protocol removal handling issue
- 8.10 Missing _disableinitializers() function call
- 8.11 Permission revocation failure in blockcompound function
- 8.12 Missing pausing/unpausing mechanism
- 8.13 Missing index update in withdrawfees function
- 8.14 Unoptimized for loops
- 8.15 Inconsistent reentrancy protection pattern in admin functions
- 8.16 Missing events
- 8.17 Unhandled return values
- 8.18 Inconsistent withdrawal pattern in withdrawfees() function
- 8.19 Missing input validation
- 8.20 Ordering for nonreentrant modifier
- 8.21 Public functions can be marked external
- 8.22 Use of revert strings instead of custom errors
- 8.23 Lack of named mappings
- 8.24 Use of magic numbers
- 8.25 Lack of upgradeable storage management pattern
- 8.26 Floating pragma
- 8.27 Unnecessary gas consumption due to suboptimal coding patterns
1. Introduction
Mevvy engaged Halborn to conduct a security assessment on their smart contracts beginning on March 17th, 2025 and ending on March 21st, 2025. The security assessment was scoped to the smart contracts provided to Halborn. Commit hashes and further details can be found in the Scope section of this report.
The Mevvy codebase in scope consists of a strategy implementation that automatically routes funds to highest yielding protocols, including Aave, Compound and Morpho.
2. Assessment Summary
Halborn was provided 5 days for the engagement and assigned 1 full-time security engineer to review the security of the smart contracts in scope. The engineer is a blockchain and smart contract security expert with advanced penetration testing and smart contract hacking skills, and deep knowledge of multiple blockchain protocols.
The purpose of the assessment is to:
Identify potential security issues within the smart contracts.
Ensure that smart contract functionality operates as intended.
In summary, Halborn identified some improvements to reduce the likelihood and impact of risks, which were mostly addressed by the Mevvy team. The main ones are the following:
The _withdrawOptimally() function should be updated to correctly handle its input parameter as the remaining amount needed from protocols, without recalculating or double-subtracting the contract's balance.Modify the _deposit() function to include TVL limit checks similar to those in _depositToProtocols().Modify the first deposit logic to respect TVL limits by calculating the maximum allowed amount based on the protocol's limit, even for first deposits.
3. Test Approach and Methodology
Halborn performed a combination of manual review of the code and automated security testing to balance efficiency, timeliness, practicality, and accuracy in regard to the scope of this assessment. While manual testing is recommended to uncover flaws in logic, process, and implementation; automated testing techniques help enhance coverage of smart contracts and can quickly identify items that do not follow security best practices.
The following phases and associated tools were used throughout the term of the assessment:
Research into architecture, purpose and use of the platform.
Smart contract manual code review and walkthrough to identify any logic issue.
Thorough assessment of safety and usage of critical Solidity variables and functions in scope that could led to arithmetic related vulnerabilities.
Local testing with custom scripts (
Foundry).Fork testing against main networks (
Foundry).Static analysis of security for scoped contract, and imported functions (
Slither).
4. Static Analysis Report
4.1 Description
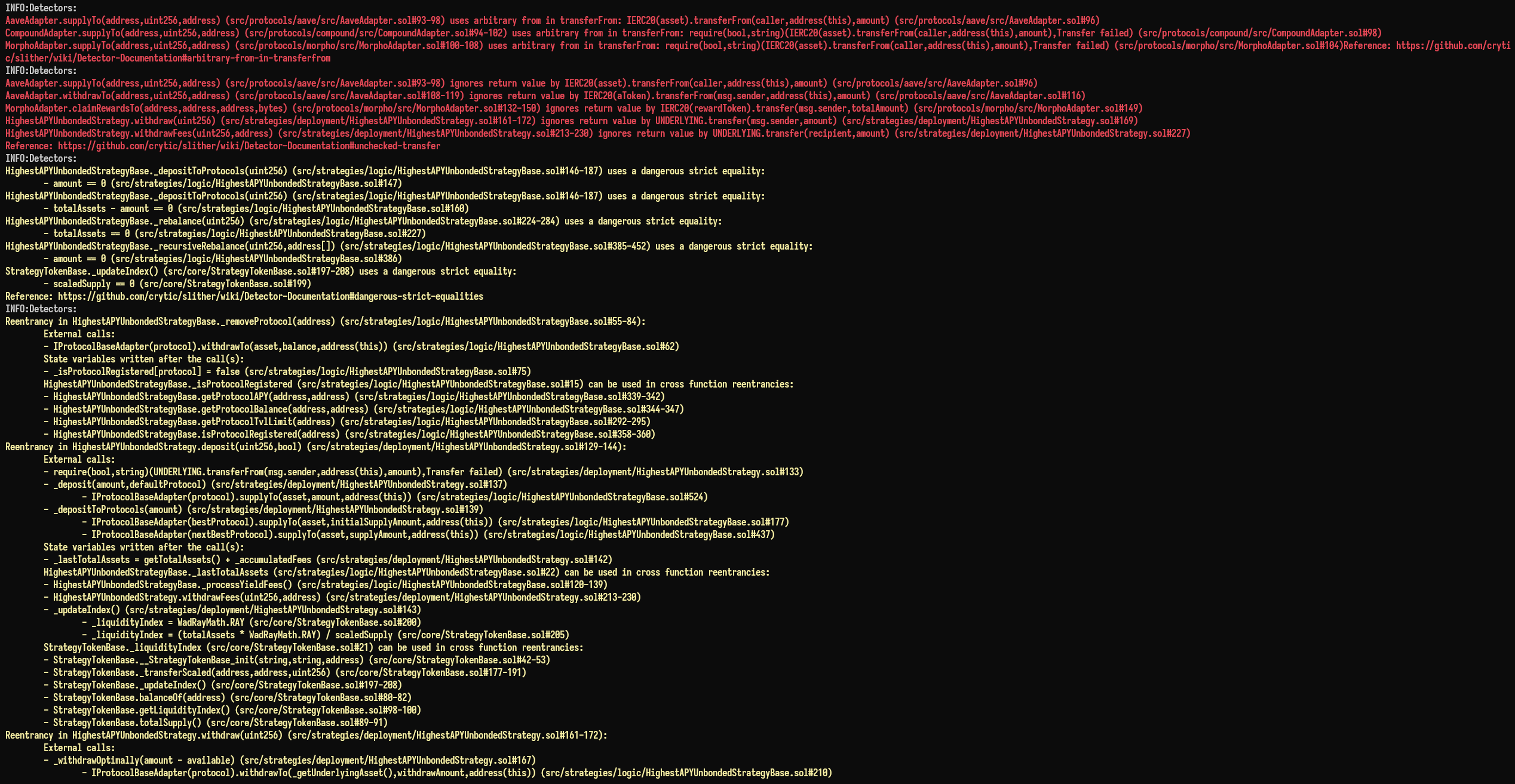
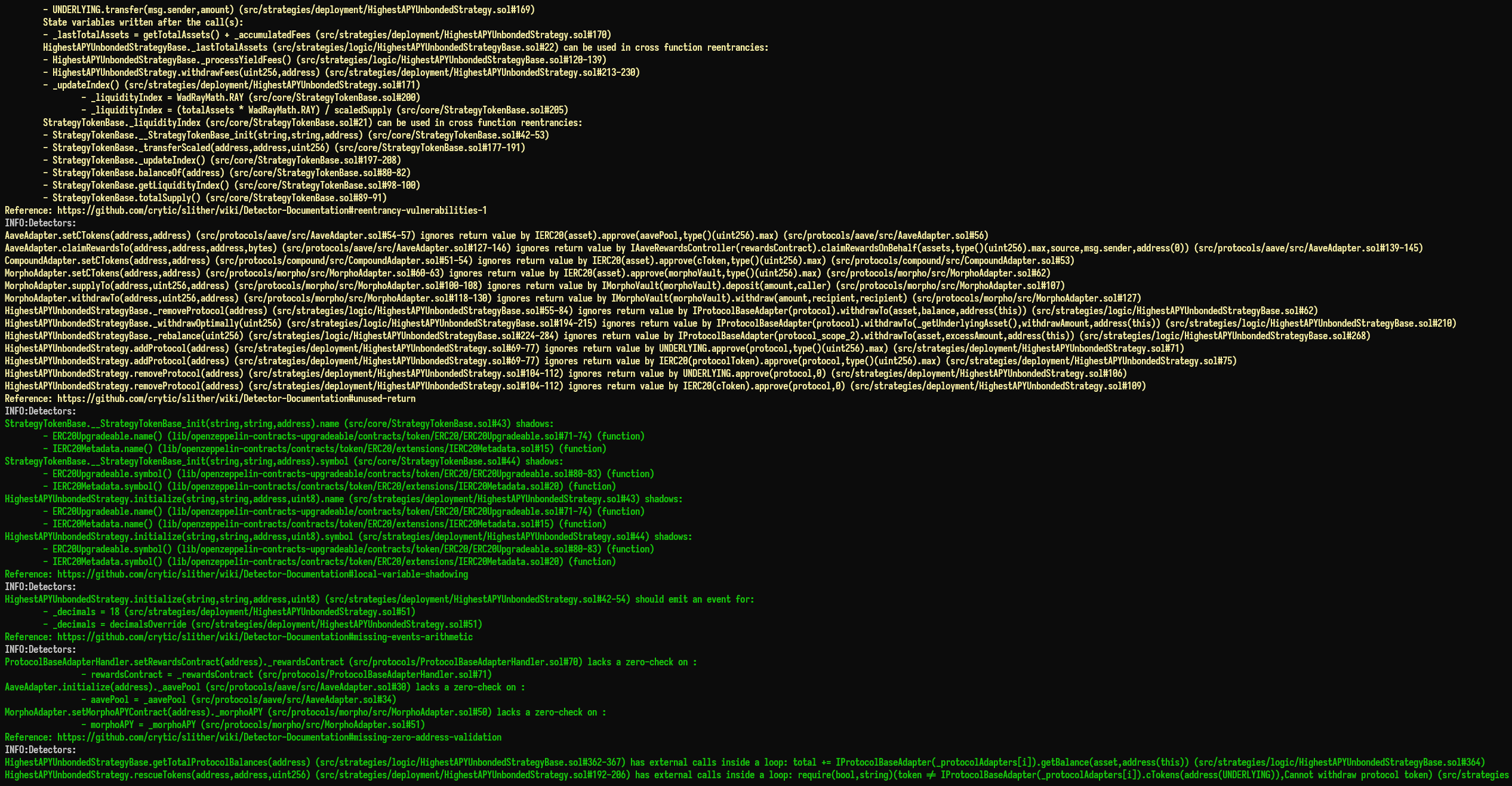
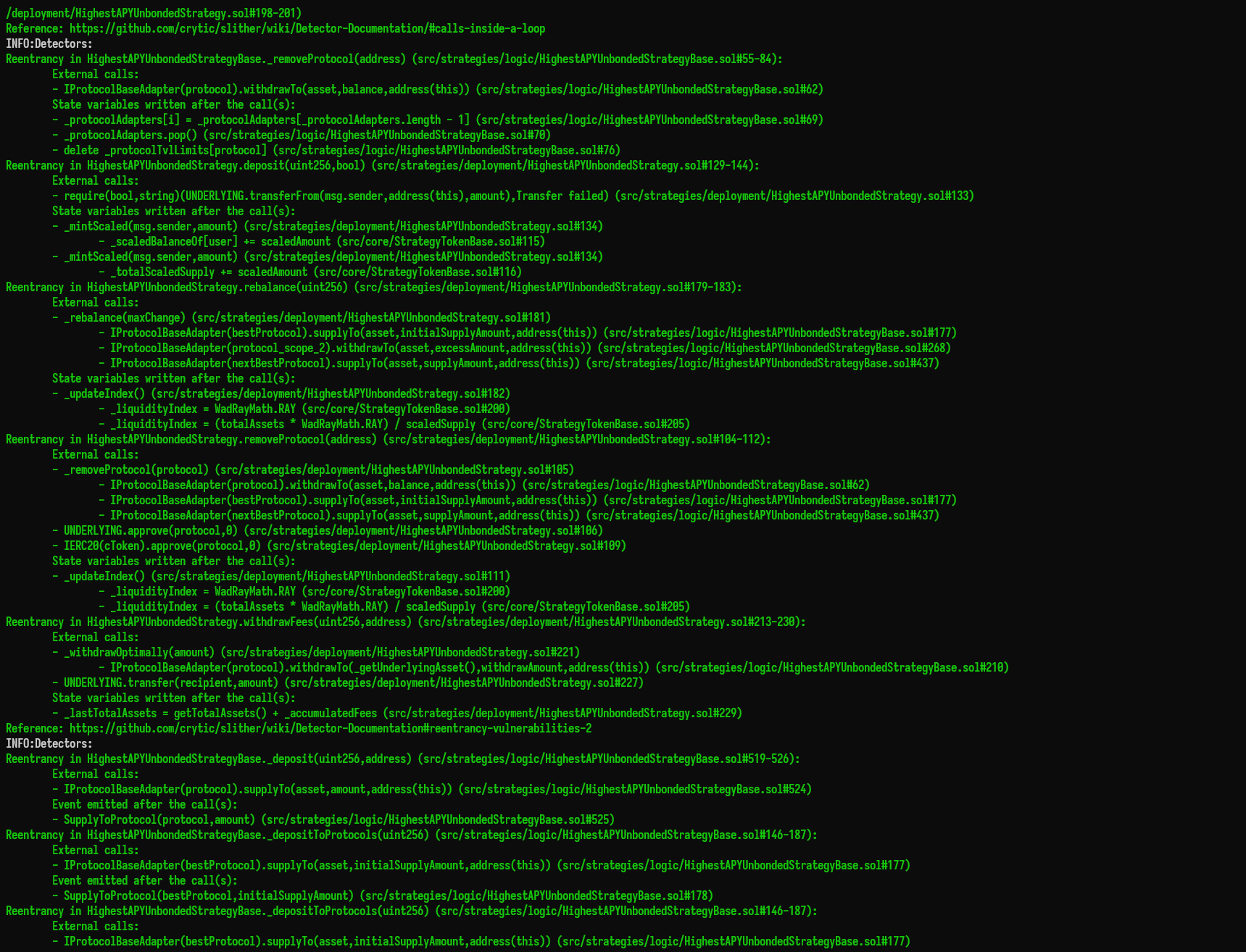
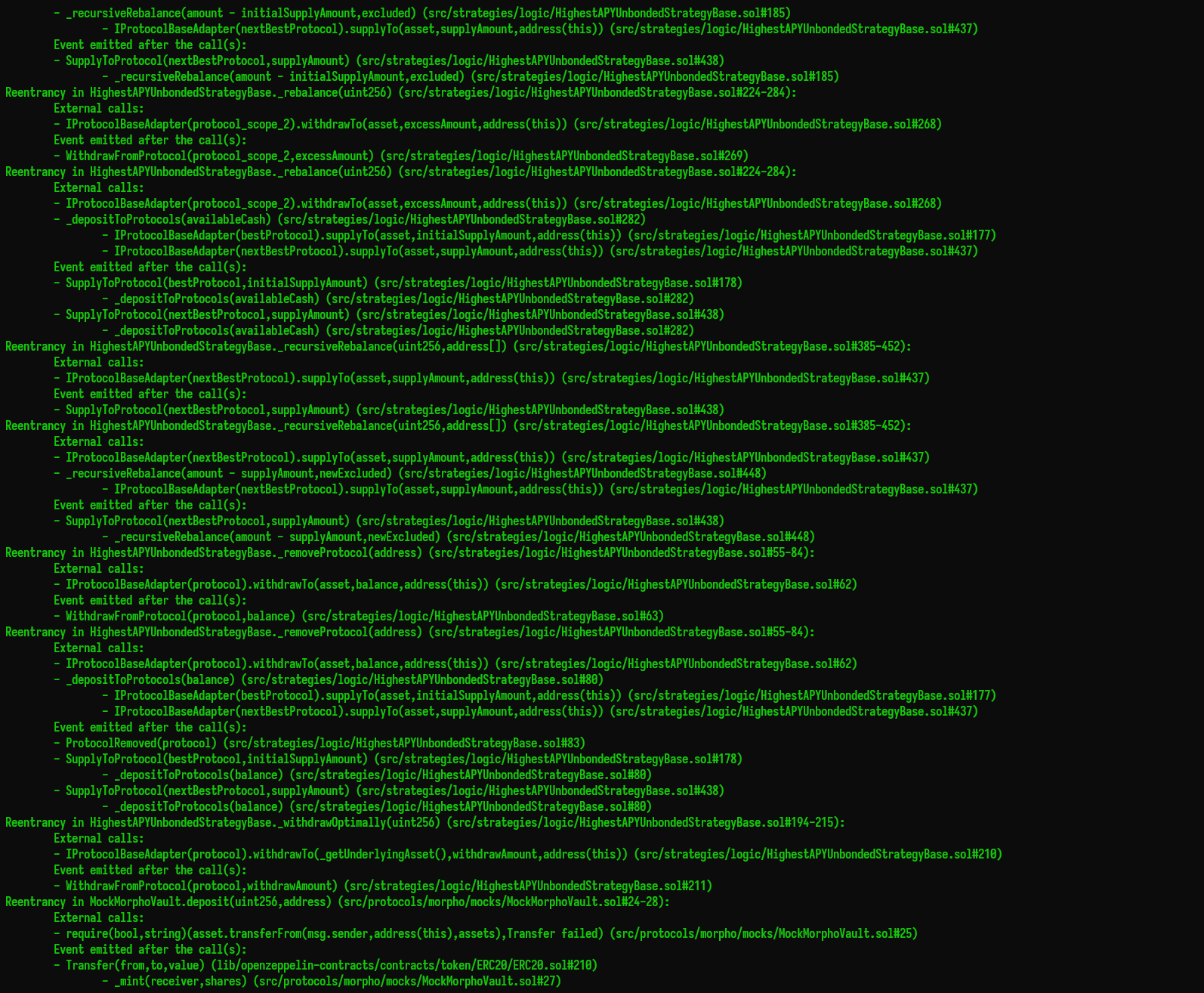
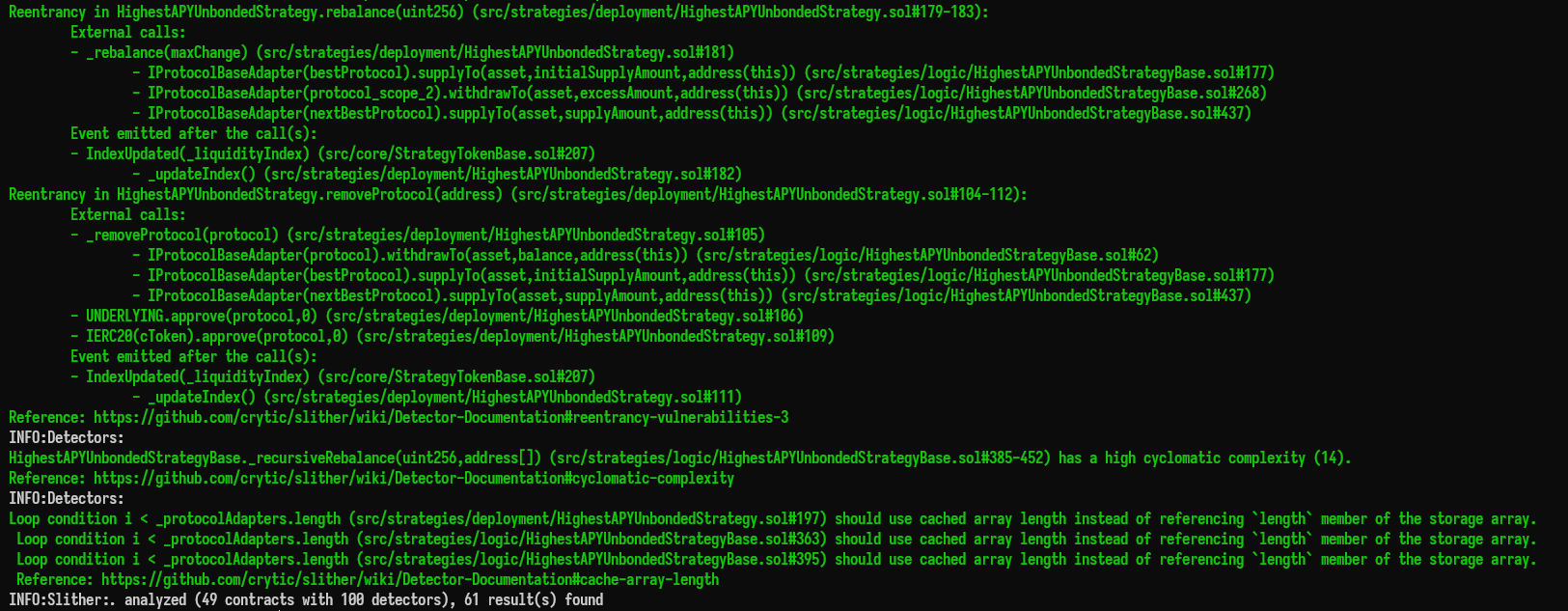
Halborn used automated testing techniques to enhance the coverage of certain areas of the smart contracts in scope. Among the tools used was Slither, a Solidity static analysis framework. After Halborn verified the smart contracts in the repository and was able to compile them correctly into their abis and binary format, Slither was run against the contracts. This tool can statically verify mathematical relationships between Solidity variables to detect invalid or inconsistent usage of the contracts' APIs across the entire code-base.
The security team assessed all findings identified by the Slither software, however, findings with related to external dependencies are not included in the below results for the sake of report readability.
4.2 Output
The findings obtained as a result of the Slither scan were reviewed, and many were not included in the report because they were determined as false positives.
5. RISK METHODOLOGY
5.1 EXPLOITABILITY
Attack Origin (AO):
Attack Cost (AC):
Attack Complexity (AX):
Metrics:
| EXPLOITABILITY METRIC () | METRIC VALUE | NUMERICAL VALUE |
|---|---|---|
| Attack Origin (AO) | Arbitrary (AO:A) Specific (AO:S) | 1 0.2 |
| Attack Cost (AC) | Low (AC:L) Medium (AC:M) High (AC:H) | 1 0.67 0.33 |
| Attack Complexity (AX) | Low (AX:L) Medium (AX:M) High (AX:H) | 1 0.67 0.33 |
5.2 IMPACT
Confidentiality (C):
Integrity (I):
Availability (A):
Deposit (D):
Yield (Y):
Metrics:
| IMPACT METRIC () | METRIC VALUE | NUMERICAL VALUE |
|---|---|---|
| Confidentiality (C) | None (C:N) Low (C:L) Medium (C:M) High (C:H) Critical (C:C) | 0 0.25 0.5 0.75 1 |
| Integrity (I) | None (I:N) Low (I:L) Medium (I:M) High (I:H) Critical (I:C) | 0 0.25 0.5 0.75 1 |
| Availability (A) | None (A:N) Low (A:L) Medium (A:M) High (A:H) Critical (A:C) | 0 0.25 0.5 0.75 1 |
| Deposit (D) | None (D:N) Low (D:L) Medium (D:M) High (D:H) Critical (D:C) | 0 0.25 0.5 0.75 1 |
| Yield (Y) | None (Y:N) Low (Y:L) Medium (Y:M) High (Y:H) Critical (Y:C) | 0 0.25 0.5 0.75 1 |
5.3 SEVERITY COEFFICIENT
Reversibility (R):
Scope (S):
Metrics:
| SEVERITY COEFFICIENT () | COEFFICIENT VALUE | NUMERICAL VALUE |
|---|---|---|
| Reversibility () | None (R:N) Partial (R:P) Full (R:F) | 1 0.5 0.25 |
| Scope () | Changed (S:C) Unchanged (S:U) | 1.25 1 |
| Severity | Score Value Range |
|---|---|
| Critical | 9 - 10 |
| High | 7 - 8.9 |
| Medium | 4.5 - 6.9 |
| Low | 2 - 4.4 |
| Informational | 0 - 1.9 |
6. SCOPE
- contracts/core/libraries/WadRayMath.sol
- contracts/protocols/aave/src/AaveAdapter.sol
- contracts/protocols/compound/src/CompoundAdapter.sol
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/9/commits/cd86b8e67e38fa1833e16067bcb2bc089f6236e3
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/14/commits/2a481b8c41ddff010553f322fdeb3cc396013c8c
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/10/commits/1e14a856cd7342775d78fbe076c853aab1bb124d
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/17/commits/aaa4675d40762fb97119133f9aa84ffed211b518
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/18/commits
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/19/commits/1b2c320a8980551eae0180dd778ae6ef95f788a7
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/16/commits/bdcb598a1dc0a99a782509a66f2213c2df18c023
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/13/commits/68d8ece4f4db8544c18096b4cd7a1ca21449e505
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/11/commits/6b1910b74422f95057934c78ff0e89c57071b088
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/20/commits/132ee341b05d9797650362d2c1094b4c875e7283
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/12/commits/0a4a25679d22a7df3e7477a22eea110a077403d6
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/31/commits/da8e0b50ce845bb525449514840cd05bd3b1eefc
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/22/commits/8a259ee5f0fde468b0c142d71091e0b5fe81ed97
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/30/commits/af549c9321b85556b44ceb2c6dffa5f9b1de2fdb
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/21/commits/dac746857bdc1662942b9448dba28c6b55bb0732
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/15/commits/6714e009d8840bda22018061ea8f4c1c7250d543
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/25/commits/971941967736d00fa1976a596cd1f487e647c4b5
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/29/commits/96b722d129b399c3a8824ca242e5510819465b4e
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/24/commits/729370cc4c2c09e60a507c6424e76ef5f07099ac
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/26/commits/e0fb94fc01e2f748bff7a35e1c13a38b19deb18f
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/27/commits/6a77b17ec725188d06e95183f5929579738d20f8
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/33/commits/596c64949986321b67f0ea85f1ea44560f4c29dd
- https://github.com/SiloMEV/mevvy-yield-contracts/pull/32/commits/d9f69740db501176f0ce1e4d9fc0486b86ee2ccb
7. Assessment Summary & Findings Overview
Critical
0
High
1
Medium
3
Low
7
Informational
16
| Security analysis | Risk level | Remediation Date |
|---|---|---|
| Impossibility to withdraw assets across protocols | High | Solved - 03/21/2025 |
| Missing TVL limit check in default protocol deposits | Medium | Risk Accepted - 03/26/2025 |
| TVL limit bypass on first deposit | Medium | Solved - 03/25/2025 |
| Revenue loss due to missing fee processing in withdrawFees() | Medium | Solved - 03/23/2025 |
| Unallocated funds without notification when protocols reach TVL limits | Low | Solved - 03/25/2025 |
| TVL limit bypass after complete withdrawal | Low | Solved - 03/25/2025 |
| Single step ownership transfer process | Low | Solved - 03/26/2025 |
| Use of non-compliant tokens may break contract functionality | Low | Solved - 03/26/2025 |
| Default protocol removal handling issue | Low | Solved - 03/26/2025 |
| Missing _disableInitializers() function call | Low | Solved - 03/23/2025 |
| Permission revocation failure in blockCompound function | Low | Solved - 03/23/2025 |
| Missing pausing/unpausing mechanism | Informational | Solved - 03/26/2025 |
| Missing index update in withdrawFees function | Informational | Solved - 03/23/2025 |
| Unoptimized for loops | Informational | Solved - 03/28/2025 |
| Inconsistent reentrancy protection pattern in admin functions | Informational | Solved - 03/27/2025 |
| Missing events | Informational | Solved - 03/28/2025 |
| Unhandled return values | Informational | Acknowledged - 03/26/2025 |
| Inconsistent withdrawal pattern in withdrawFees() function | Informational | Solved - 03/21/2025 |
| Missing input validation | Informational | Solved - 03/27/2025 |
| Ordering for nonReentrant modifier | Informational | Solved - 03/25/2025 |
| Public functions can be marked external | Informational | Solved - 03/27/2025 |
| Use of revert strings instead of custom errors | Informational | Solved - 03/28/2025 |
| Lack of named mappings | Informational | Solved - 03/27/2025 |
| Use of magic numbers | Informational | Solved - 03/27/2025 |
| Lack of upgradeable storage management pattern | Informational | Solved - 03/27/2025 |
| Floating pragma | Informational | Solved - 03/28/2025 |
| Unnecessary gas consumption due to suboptimal coding patterns | Informational | Solved - 03/28/2025 |
8. Findings & Tech Details
8.1 Impossibility to withdraw assets across protocols
//
Description
Proof of Concept
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.2 Missing TVL limit check in default protocol deposits
//
Description
BVSS
Recommendation
Remediation Comment
References
8.3 TVL limit bypass on first deposit
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.4 Revenue loss due to missing fee processing in withdrawFees()
//
Description
Proof of Concept
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.5 Unallocated funds without notification when protocols reach TVL limits
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.6 TVL limit bypass after complete withdrawal
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.7 Single step ownership transfer process
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.8 Use of non-compliant tokens may break contract functionality
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.9 Default protocol removal handling issue
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.10 Missing _disableInitializers() function call
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.11 Permission revocation failure in blockCompound function
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.12 Missing pausing/unpausing mechanism
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.13 Missing index update in withdrawFees function
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.14 Unoptimized for loops
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.15 Inconsistent reentrancy protection pattern in admin functions
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.16 Missing events
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.17 Unhandled return values
//
Description
BVSS
Recommendation
Remediation Comment
References
8.18 Inconsistent withdrawal pattern in withdrawFees() function
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.19 Missing input validation
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.20 Ordering for nonReentrant modifier
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.21 Public functions can be marked external
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.22 Use of revert strings instead of custom errors
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.23 Lack of named mappings
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.24 Use of magic numbers
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.25 Lack of upgradeable storage management pattern
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.26 Floating pragma
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
8.27 Unnecessary gas consumption due to suboptimal coding patterns
//
Description
BVSS
Recommendation
Remediation Comment
Remediation Hash
References
Halborn strongly recommends conducting a follow-up assessment of the project either within six months or immediately following any material changes to the codebase, whichever comes first. This approach is crucial for maintaining the project’s integrity and addressing potential vulnerabilities introduced by code modifications.
Table of Contents
- 1. Introduction
- 2. Assessment summary
- 3. Test approach and methodology
- 4. Static analysis report
- 5. Risk methodology
- 6. Scope
- 7. Assessment summary & findings overview
- 8. Findings & Tech Details
- 8.1 Impossibility to withdraw assets across protocols
- 8.2 Missing tvl limit check in default protocol deposits
- 8.3 Tvl limit bypass on first deposit
- 8.4 Revenue loss due to missing fee processing in withdrawfees()
- 8.5 Unallocated funds without notification when protocols reach tvl limits
- 8.6 Tvl limit bypass after complete withdrawal
- 8.7 Single step ownership transfer process
- 8.8 Use of non-compliant tokens may break contract functionality
- 8.9 Default protocol removal handling issue
- 8.10 Missing _disableinitializers() function call
- 8.11 Permission revocation failure in blockcompound function
- 8.12 Missing pausing/unpausing mechanism
- 8.13 Missing index update in withdrawfees function
- 8.14 Unoptimized for loops
- 8.15 Inconsistent reentrancy protection pattern in admin functions
- 8.16 Missing events
- 8.17 Unhandled return values
- 8.18 Inconsistent withdrawal pattern in withdrawfees() function
- 8.19 Missing input validation
- 8.20 Ordering for nonreentrant modifier
- 8.21 Public functions can be marked external
- 8.22 Use of revert strings instead of custom errors
- 8.23 Lack of named mappings
- 8.24 Use of magic numbers
- 8.25 Lack of upgradeable storage management pattern
- 8.26 Floating pragma
- 8.27 Unnecessary gas consumption due to suboptimal coding patterns
// Download the full report
Yield Contracts
* Use Google Chrome for best results
** Check "Background Graphics" in the print settings if needed
